Cyber Security Bootcamp
With the increasing integration of systems and reliance on digital data in organizations and businesses, the need for cybersecurity teams has become critical to protect against growing digital threats.
Technology companies are prime targets for cyber attacks due to the amount of sensitive data and vital information they hold. That’s why internal cyber teams are an integral part of a company’s overall security strategy. They regularly scan systems and applications, analyze potential threats, and develop effective defense strategies. Thanks to these efforts, the company’s technology infrastructure is strengthened and security risks are reduced.
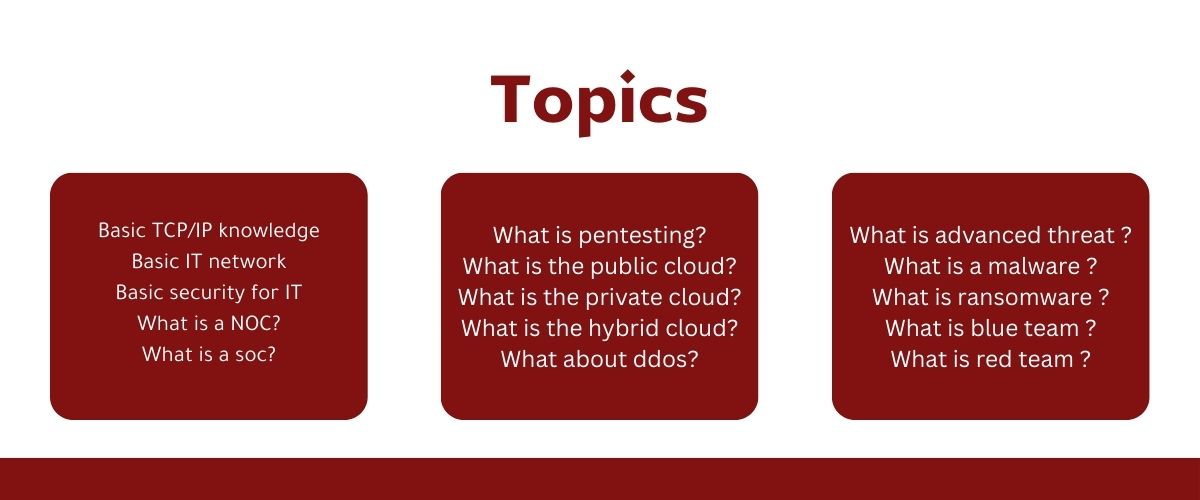
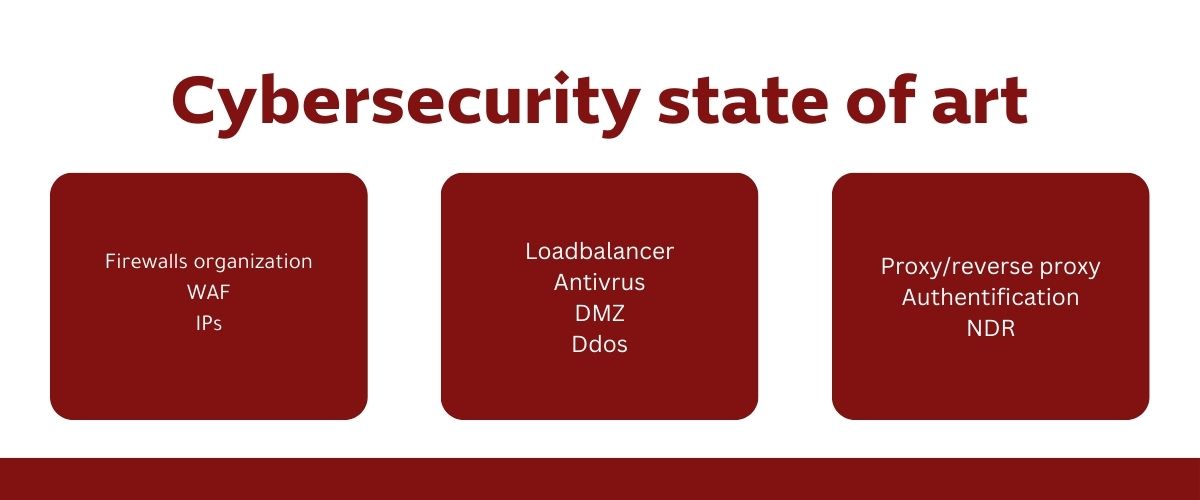
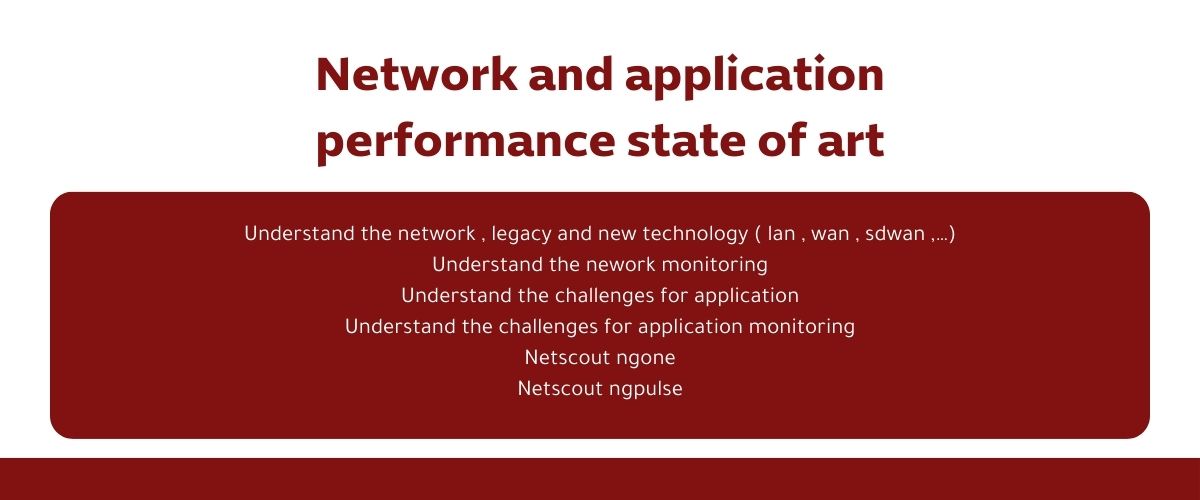




Cyber Security Bootcamp Q & A
Qualifying participants to work within cyber security teams to protect institutions and companies.
Training on protection tools and network monitoring.
20 trainees in each camp from students and new graduates
Intensive training on networking principles and the latest cybersecurity technologies from one of the world's leading cybersecurity companies.
Learn network monitoring and protection tools
Join a community of technologists and developers.
Practical activities, training and awareness workshops.
A certificate accredited by the academy.
6 weeks – 180 training hours
150 hours of work and study.
Knowledge of networking and cloud computing basics.
The applicant must be between 28 and 20 years old.
Pass the competitive exam and personal interview.
Educational materials to prepare for the competitive exam
1.Getting Started in IT https://vmware.bravais.com/s/bjOyL9ppvPttxD6BefbO
2.Cloud and Virtualization Concepts https://www.netdevgroup.com/online/courses/cloud/cloud-and-virtualization-concepts
